Nessus Professional Setup Requirements
The minimum setup requirements for Nessus Professional for Vulnerability Assessments.
We are often asked about using Nessus Professional which is installed and in use within organisations when completing our own assessments. We are of course happy to do so, with the requirement that, our assessor has "hands-on" access to your Nessus deployment to check the setup of the jobs and that the scans are working correctly.
On numerous occasions, our assessors have inspected a customer's Nessus Professional deployment and associated scans and found that the scans are not gathering all the correct information as the scanner doesn't have the access required, on Windows, Mac OS X and Linux.
Nessus, when working on the LAN, can only access a level of the security account you provide, and of course, that also requires that account to have the correct access on the device itself.
WHAT WE WILL REQUIRE
We will require an export of your Nessus Scan Jobs, locked with a password we will agree with you at the time, so we can import these into our Nessus Professional, and review these for compliance.
If you are able to send us database exports of your scans in advance of your assessment, we can also ensure you are configured correctly and provide any associated advice.
THE EXPORT
From within a scan task, from the menu, select the Export option, and select Nessus DB
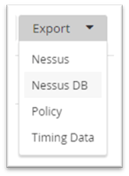
You will then be asked to provide a password for the database export
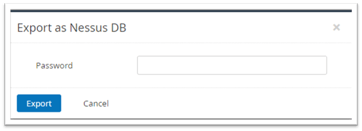
When you have entered a suitable password (which you will share with us) you can click on the Export button, where you will then be asked to save the export file.
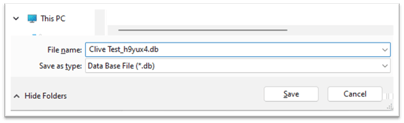
Once you have your file(s), we suggest Zipping them up (as they may actually be very large, if your job has a lot of history) and then emailing them over to our assessment team.
NOTE: During the actual assessment, our assessor will still have "hands-on" on your Nessus instance to check things, but the above, allows us to do so remotely, in the first instance.
GENERAL REQUIREMENTS
WINDOWS
There are a number of requirements that Nessus has for the successful scanning of Windows devices and they include:
Our setup help article can be found here
- A suitable username and password with sufficient access for
- WMI/DCOM Access
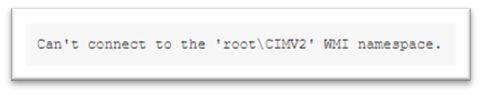
- SMB Access
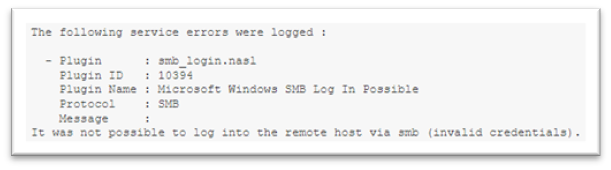
- Device Authentication
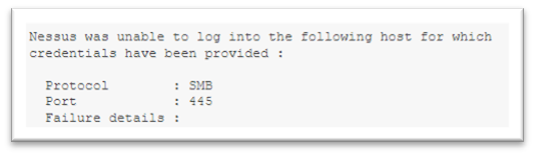
- WMI/DCOM Access
- The LocalAccountTokenFilterPolicy registry key set
- Firewall rules to allow scanning to happen
APPLE OS
There are a number of requirements that Nessus has for the successful scanning of Apple Mac devices, which, based on Unix, and similar to Linux, are the same as those required for Linux and they include:
Our setup help article can be found here
- Suitable Username / Password for user and root access to deliver
- SSH Access as a root / sudoer
- Device Authentication
- Gatekeeper Firewall rules to allow scanning to happen
LINUX
Very similar to that of Apple OS X, Linux requires SSH and sudoers access, along with firewall (IPTABLES etc) rules in order to scan correctly.
Our setup help article can be found here